How can merchants get compliant with the Visa Stored Credential Transaction framework and mandates effective October 14, 2017? Most companies are under the false impression that their acquirer and or payment gateway manages compliance. Not true. While some technical aspects are managed by the payment gateway, the merchant also has to make some changes for compliance.
What is a Stored Credential? A stored credential is information (including, but not limited to, an account number or payment token) that is stored to process future purchases for a cardholder.
What is the Visa Stored Credential framework and mandate? It outlines the rules related to storing and using stored credentials. Since it’s 15 pages long, I’ll only highlight a few important items here.
- Merchant initiated or customer initiated transactions? Make sure your payment gateway is sending the correct code. For example, an ecommerce store checkout would be customer initiated. A recurring billing transaction is merchant initiated.
- Get customer consent for terms and conditions of storing and using stored card.
- Advise how the cardholder will be notified of any changes to the consent agreement.
- For a transaction using a stored credential initiated by the cardholder, the merchant or its agent must validate the cardholder’s identity before processing. The only valid methods are 3-D Secure Verified by Visa and the security code.
- Receipt must be provided for the initial cardholder validation ($0 dollar transaction or actual amount.)
- All stored credential transactions must be submitted with a value of “10” in the POS Entry Mode Code field; this is for both newly stored cards and all prior transactions using stored credential. This is managed by the payment gateway. (Confirm your gateway is doing this.)
What about the other card brands? Mastercard rolled out their version in June 2018. If you comply with the Visa mandate, you’ll be in compliance with any others at this time.
What if I don’t comply?
- You’ll be non-compliant with Visa’s rules and risk Non Compliance Assessments
- No benefit from expected improved authorization rate
- Increased customer complaints and poor cardholder experience
- Cannot use Real Time Visa Account Updater service
- Risk issuer generated chargebacks for all transactions using the stored credential within the allowable chargeback timeframe under reason code 72, invalid authorization. A valid authorization is needed to qualify for the lowest interchange rates.
What are the benefits of compliance? Increased authorizations, better customer experience, more profits.
See Improving Authorization Management for Transactions with Stored Credentials https://usa.visa.com/dam/VCOM/global/support-legal/documents/stored-credential-transaction-framework-vbs-10-may-17.pdf . Are you going to manage documenting everything or are you going to use technology to help you manage it?
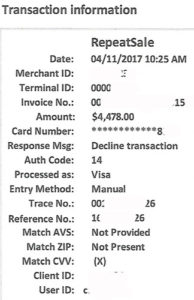
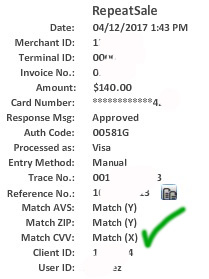
Verify if you have a system to manage authorization validity. What the heck does that mean? Many companies have complex needs including pre-authorizations, incremental authorizations, delayed shipping etc. While you may get issuer approvals, that doesn’t mean the authorization is valid. Are you compliant now? Look at your merchant statement ‘pending interchange fees. If you see EIRF or STD or misuse of authorization fee, there’s a problem.
Replace paper credit card authorization forms, and any digital form that you can decrypt and view sensitive card data. Offer your customers a way to self-manage their own wallet with either a hosted online pay page or Electronic Bill Presentment & Payment.
New to online payments? See Visa best practices to prevent brute force attacks. https://usa.visa.com/support/merchant/library/visa-merchant-business-news-digest.html. CenPOS includes recaptcha and client managed velocity and other rules as part of a layered security approach.
Register for 3-D Secure, including Verified by Visa, with your acquirer. Don’t do this until you know which payment gateway will be used and get their instructions if applicable.
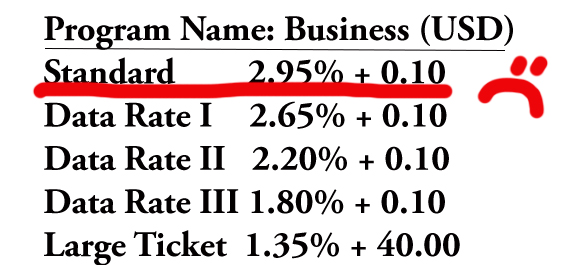
The same transaction can process at different rates as shown above, depending on which rules you follow. CenPOS Smart Rate Selector automates compliance to qualify transactions at the lowest rate possible. Which rates are on your merchant statement now?
Where can I buy CenPOS or learn more? You’ve already found one of the top salespeople, Christine Speedy. All agreements are direct with CenPOS, no middle man.
Resources and documentation https://3dmerchant.com/blog/merchant-bulletins-downloads – bookmark it!. Join Christine Speedy’s email list.
DISCLAIMER: condensed and incomplete information! Information may be quickly outdated.
With the fast pace of changing rules, companies need a technology partner to automate compliance. Did you know?
- CenPOS has a suite of solutions for companies just like yours, solving common problems and increasing profits virtually overnight.
- For those not ready to give up paper, CenPOS creates a printable PCI Compliant credit card authorization form for every stored card.
- CenPOS has ERP, ecommerce shopping cart, accounting and other plug-in modules available for quick and easy implementation.
- I’ve been selling for CenPOS since day 1. Though I have other payment gateways available in my arsenal, nothing else compares.
Call Christine Speedy for global sales. 954-942-0483, 9-5 ET, CenPOS authorized reseller based out of South Florida and NY. CenPOS is an integrated commerce technology platform driving innovative, omnichannel solutions tailored to meet a merchant’s market needs. Providing a single point of integration, the CenPOS platform combines payment, commerce and value-added functionality enabling merchants to transform their commerce experience, eliminate the need to manage complex integrations, reduce the burden of accepting payments and create deeper customer relationships.