Free credit card transaction fees checkup includes self-assessment, no merchant statement sharing with third party required. Due to massive changes in card network rules over the last two years, a review is essential. This method is easier than my B2B credit card processing fact check, while still revealing problems that must be resolved. As a processor neutral payments expert, Christine Speedy offers a unique perspective.
Here’s a shortcut to determine if you have authorization problems, which directly impact credit card transaction fees. Why is this important? Because unless you fix the underlying problem, switching merchant accounts will only provide partial relief from escalating transaction fees like the new MasterCard .25% misuse of authorization fee. If you have any of these items below on your merchant statement, you have a problem. Most likely it’s a payment gateway issue.
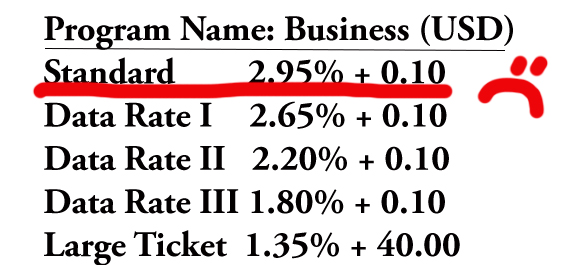
- Misuse
- Integrity
- Compliance or Non-compliance
- Standard / STD (any)
- EIRF
- Data rate I
- Data Rate II or Data Rate 2
- Chargeback: FRAUD TRANS-NO CARDHOLDR AUTH
- Chargeback reason: Compliance
Hint: If you open your merchant statement in Adobe Acrobat, in OSX with command F you can copy and paste the terms above. It’s not foolproof due to varying abbreviations, but you only need to have one of the bad items to know there’s a problem.
For card not present business to business, merchants should see these two interchange types:
- Full UCAF
- Data Rate III
I don’t know why, but I get calls from other salespeople in the industry looking for solutions to help customers qualify for Data Rate II. Why wouldn’t you want the customer to qualify at Data Rate III? Makes no sense.
I also hear from merchants how they were told that the new solution would fix their level 3 data problems, but it didn’t. If you do preauthorizations, and the solution doesn’t automatically get new authorizations and manage reversals it’s not going to fix authorization problems. Always ask, “how will the payment gateway manage authorization reversals if we don’t settle for the original preauthorization amount’? That’s one of several critical key questions. If they don’t know the answer instantly, move on.
Due to massive changes in card network rules and data security compliance rules over the last two years, a review by a neutral payments expert is essential. Did you have any red items? It’s time for a deeper dive into why. Your FREE report will identify issues impacting profits and security, include action items how to fix them, and rarely requires changing financial partners.
Your FREE report will identify issues impacting profits and security, include action items how to fix them, and won’t require changing financial partners (in most cases).
Call Christine Speedy, PCI Council QIR certified, to reduce merchant fees with new or existing merchant account at 954-942-0483, 9-5 ET. CenPOS authorized reseller based out of South Florida and NY. CenPOS is an integrated commerce technology platform driving innovative, omnichannel solutions tailored to meet a merchant’s market needs. Providing a single point of integration, the CenPOS platform combines payment, commerce and value-added functionality enabling merchants to transform their commerce experience, eliminate the need to manage complex integrations, reduce the burden of accepting payments and create deeper customer relationships.