Credit card authorization form 2019 templates are starting to pop up on the internet. The forms are never PCI compliant nor compliant with card network rules, plus the form might introduce malicious code into your network, leading to a future data breach. In this article learn about compliant credit card authorization form problems and solutions.
Merchants must replace traditional credit card authorization forms with other payment methods where the customer self-pays in 2019. The services are typically provided by a payment gateway, acquirer or software solutions provider. I recommend using an independent payment gateway for the checkout because if other changes are made, such and changing acquirer, it’s non-disruptive to customers and business processes.
Three solutions to replace traditional credit card authorization forms:
- Hosted pay page is a third party hosted web page where buyer can enter all their payment information for immediate payment, and in some cases store it for future payments.
- Pushing out a payment request via text or email includes link to a hosted prefilled pay page that can include an invoice number and amount due.
- Electronic invoicing may be standalone or integrated and empowers buyers to pay online.
Per Visa, merchants are never allowed to ask for the security code in any written form. Merchants also cannot store the form with full card numbers nor store the security code after authorization. Traditional credit card authorization forms increase risk of fraud and identity theft and nobody likes them!
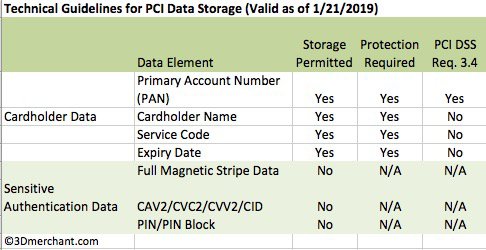
Cardholder verification with 3-D Secure shifts fraud liability to the issuer, so instead of responding to chargebacks, merchants can prevent them from happening. This is far more powerful than using security code or address for cardholder verification, and eliminates the need for traditional credit card authorization forms. 3-D Secure is a set of global security standards, for example, Verified by Visa.
Phone order payments risk identity theft:
- Phone orders expose card data to employees.
- Employees often write the cardholder information down on paper first to avoid making a mistake that requires them asking for the information again.
- While less than 15% of data breaches occur from insider threats, trusted employees do steal data for financial, espionage, and grudge reasons.
- It costs more to process the card both in actual labor and in card acceptance fees because it’s impossible to qualify for the lowest card not present rates possible on manually key-entered transactions.
Fax order payments risk identity theft:
- All of the phone order risks apply, plus new risks for fax.
- Digital faxes have memory where data can be stored, risking theft during use and after disposal of hardware.
- Depending on access to the hardware or software, many people might have access to faxed forms, including evening cleaning service personnel.
- Merchants cannot ask for security code on the form, yet it’s required for card not present transactions.
- The card number must be masked after use if being stored
- Storing the form has no value because if proper card not present rules are followed, there’s no need for it to defend chargebacks.
Cloud digital credit card authorization forms may not be PCI compliant:
The rise in digital credit card authorization forms is downright scary, because despite claims by sellers, merchant implementation of them is often not PCI Compliant. Here’s a few reasons why:
- Neither merchants nor third parties can store the security code after authorization.
- Neither merchants nor third parties can store the card number unmasked after authorization.
- Merchants will be hard pressed to prove PCI Compliance in the event of a data breach. Who had access to the forms and when? How is the server wiped of the data? What about back up servers?
- What’s the point of getting a signed form if you can’t save it?
- If the service offers an authorization to verify cardholder, but the merchant then types card number into another system with no connection to the initial verification, all subsequent transactions are in violation of rules for storing and using stored cards thus are open to issuer chargeback risk.
Benefits of compliant solution:
- Reduced merchant fees for some cards (3-D Secure cardholder authentication such as Verified by Visa must be enabled.)
Increased approvals with cardholder authentication.
Mitigate chargeback risk – with 3-D Secure cardholder authentication, fraud liability shifts to issuer.
More convenient for buyers- 24/7 payments on their schedule, not yours.
Buyers are in control of choosing to store payment methods
How can merchants get 3-D Secure? Contact us for the latest instructions or call your acquirer aka merchant services provider.
Call Christine Speedy, PCI Council QIR certified, for simple solutions to card not present payment transaction problems, 954-942-0483, 9-5 ET.
References: Search the blog for credential or form or click on the navigation for links for more resources on rules and compliance.
