PCI Compliance, credit card authorization form, and CenPOS bulletin were all in the February 2016 enewsletter. Did you miss it? Subscribe here for payment news.
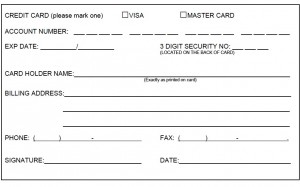
80% of companies FAIL an interim Payment Card Industry Data Security Standards (PCI-DSS) audit. It’s time to admit it- you’re company is one of the many struggling to keep up with new rules. Have you noticed $19.95 fee sneak back into your merchant statements? Check your quarterly scans. You may discover a scan failed with a reason related to SSL. Fight back to stop these monthly fees. Not only is it premature, but the Payment Card Industry Security Standards Council (PCI SSC) changed the migration to date requiring TLS 1.1 encryption or higher from June 2016 to June 2018. Credit card authorization forms – a weak link for compliance “We keep all cardholder data in a locked file drawer and I’m the only one with a key” does not comply with PCI 3.0 standards. TIPS.
Every moment a paper form exists, there’s an opportunity for misuse and identity theft. If your company extends credit, then Red Flags Rules also apply. The FTC can seek both monetary civil penalties and injunctive relief for violations. All told, the expense of a breach could run over a million dollars, uncovered by insurance, plus ongoing lost business due to damaged reputation. Is your service provider PCI Compliant? If a third party touches card data, they’re required to register with the card brands and have an annual on-site audit. That includes your payment gateway, caging service, and other software if their payments are not segregated from the applications. Click here to search the Visa service provider database Software Updates How can we collect cardholder data for B2B card not present customers without our credit card authorization form?
PCI Compliant credit card authorization form example: VideoTraining & educational videos https://www.youtube.com/user/3Dmerchant/videos Christine Speedy
CenPOS is a processor agnostic end to end payment engine that increases EBITDA virtually instantly. From compliance to automating collections, we solve everyday business problems. Protecting the front door with US EMV certified multi-lane terminals for all processors and the back door with 3-D Secure certified solutions for customer initiated sales. Now in over 140 countries. Feb 01, 2016 1:04 pm | Christine Speedy
Replacing ICVerify or other legacy software for batch credit card processing? Whether you’re in the cloud, or headed there, methods of payment processing have changed to meet current and future requirements for PCI Compliance and fraud prevention. For service providers, … Continue reading Jan 25, 2016 11:14 am | Christine Speedy
Winter Storm Jonas is a reminder of the importance for business to business companies to accept payments online. What if you have a desktop terminal, but staff is working from home? How can accounts receivable be reached for call in … Continue reading Jan 13, 2016 8:36 am | Christine Speedy
Getting a VeriFone EMV Vx520, FD55, Vx510, Vx570 CAPK expired error message? Visa has extended the EMV key’s expiration date from 12/31/2015 to 2022, and the terminal must be updated. OPTION 1: UPDATE CAPK FILE ONLY via partial download For … Continue reading Jan 12, 2016 2:04 pm | Christine Speedy
Ready to improve PCI Compliance with token billing? Step by step instructions for CenPOS card not present token billing including creating, modifying, and using tokens follows. In the virtual terminal admin, Create a new Role* or Modify an existing role … Continue reading Jan 11, 2016 12:26 pm | Christine Speedy
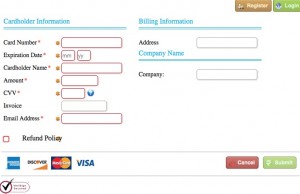
Need a 3rd party credit card authorization form template? Don’t count on wikiform.org and other internet resources that scrape the internet for free content and then redistribute it. There’s no guarantee that anything published is accurate, legal, or virus free. … Continue reading |
|
|||||||||||||||||

 For new best practices, think like a forensic auditor. In the event of a suspected breach, how will you identify who, what, when, how, and maybe even where card data was touched? Without a system to automate logging, the time and cost of an audit will explode.
For new best practices, think like a forensic auditor. In the event of a suspected breach, how will you identify who, what, when, how, and maybe even where card data was touched? Without a system to automate logging, the time and cost of an audit will explode.