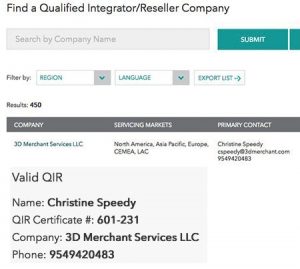
A certified Qualified Integrator and Reseller (QIR) is required for any third party credit card point-of-sale solution installation. Qualified Integrators and Resellers are specially trained by Payment Card Industry (PCI) Security Standards Council to address critical security controls while installing merchant payment systems. Christine Speedy is located in South Florida and is QIR certified. After the sale, the same applies. No third party can modify or touch the system unless QIR certified.
The mandate is only for level 4 merchants, due to more frequent security problems. For example, 80 percent of small merchant breaches are associated with insecure POS implementation and servicing by integrators and resellers. Level 4 merchants are defined as less than 20,000 Visa or MasterCard e-commerce transactions annually, and all other merchants processing up to 1 million Visa or MasterCard transactions annually.
The council changed the QIR certification requirements after my certification in an effort to reduce barriers to certification, both financially and with the depth of training. While QIR certification always was for individuals, they were tied to companies. The tie to companies has been removed so as QIR’s change jobs the certification is not disrupted. Due to this change, the PCI council recently updated the web site search navigation. My company used to be the first listing when you clicked on the QIR link. Now, the only way to find me or any other QIR certified person is to do a search. You can find Christine by searching for Christine Speedy in Florida.
Do you need a QIR in another state? Just ask.
Christine Speedy, Founder 3D Merchant Services, is a credit card processing expert with specialized expertise in card not present and omnichannel technology. Christine is an authorized reseller for Elavon and CenPOS products and services, in addition to other solutions.